用户:Ek3ru8m4/沙盒
此用户页目前正依照其他维基百科上的内容进行翻译。 (2018年4月13日) |
Shellshock,又称Bashdoor[1],是Bash shell的一系列安全漏洞[2]。最早在2014年9月24日公开。许多互联网守护进程,如网页伺服器,使用bash来处理某些命令,从而允许攻击者在易受攻击的Bash版本上执行任意代码。这可使攻击者在未授权的情况下访问电脑系统[3]。

Shellshock, also known as Bashdoor,[1] is a family of security bugs[2] in the widely used Unix Bash shell, the first of which was disclosed on 24 September 2014. Many Internet-facing services, such as some web server deployments, use Bash to process certain requests, allowing an attacker to cause vulnerable versions of Bash to execute arbitrary commands. This can allow an attacker to gain unauthorized access to a computer system.[3]
Stéphane Chazelas contacted Bash's maintainer, Chet Ramey, on 12 September 2014[1] telling Ramey about his discovery of the original bug, which he called "Bashdoor". Working together with security experts, he soon had a patch as well.[1] The bug was assigned the CVE identifier CVE-2014-6271.[4] It was announced to the public on 24 September 2014 when Bash updates with the fix were ready for distribution.[5]
The first bug causes Bash to unintentionally execute commands when the commands are concatenated to the end of function definitions stored in the values of environment variables.[1][6] Within days of the publication of this, intense scrutiny of the underlying design flaws discovered a variety of related vulnerabilities (CVE-2014-6277, CVE-2014-6278, CVE-2014-7169, CVE-2014-7186, and CVE-2014-7187); which Ramey addressed with a series of further patches.[7][8]
Attackers exploited Shellshock within hours of the initial disclosure by creating botnets of compromised computers to perform distributed denial-of-service attacks and vulnerability scanning.[9][10] Security companies recorded millions of attacks and probes related to the bug in the days following the disclosure.[11][12]
Shellshock could potentially compromise millions of unpatched servers and other systems. Accordingly, it has been compared to the Heartbleed bug in its severity.[3][13]
简介
[编辑]缺陷报告
[编辑]参考
[编辑]- ^ 1.0 1.1 1.2 1.3 1.4 Perlroth, Nicole. Security Experts Expect ‘Shellshock’ Software Bug in Bash to Be Significant. New York Times. 25 September 2014 [25 September 2014]. 引用错误:带有name属性“NYT-20140925-NP”的
<ref>标签用不同内容定义了多次 - ^ 2.0 2.1 虽然一些消息来源将Shellshock称为“病毒”,但它其实是某些操作系统自带程序中的编写错误。参见 => Staff. What does the "Shellshock" bug affect?. The Safe Mac. 25 September 2014 [27 September 2014]. 引用错误:带有name属性“TSM-20140927”的
<ref>标签用不同内容定义了多次 - ^ 3.0 3.1 3.2 Seltzer, Larry. Shellshock makes Heartbleed look insignificant. ZD Net. 29 September 2014 [29 September 2014]. 引用错误:带有name属性“ZDN-20140929”的
<ref>标签用不同内容定义了多次 - ^ Florian Weimer. oss-sec: Re: CVE-2014-6271: remote code execution through bash. Seclists.org. 24 September 2014 [1 November 2014].
- ^ Florian Weimer. oss-sec: Re: CVE-2014-6271: remote code execution through bash. Seclists.org. 24 September 2014 [1 November 2014].
- ^ Leyden, John. Patch Bash NOW: 'Shell Shock' bug blasts OS X, Linux systems wide open. The Register. 24 September 2014 [25 September 2014].
- ^ 引用错误:没有为名为
ITN-20140929的参考文献提供内容 - ^ 引用错误:没有为名为
zdnet-betterbash的参考文献提供内容 - ^ 引用错误:没有为名为
Wired的参考文献提供内容 - ^ 引用错误:没有为名为
IT-20140926-JS的参考文献提供内容 - ^ 引用错误:没有为名为
NYT-20140926-NP的参考文献提供内容 - ^ 引用错误:没有为名为
businessweek的参考文献提供内容 - ^ Cerrudo, Cesar. Why the Shellshock Bug Is Worse than Heartbleed. MIT Technology Review. 30 September 2014 [1 October 2014].
概述
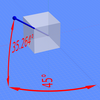
[编辑]各座标轴之间角度相等(120°)的视角,就是等角的观点。以正方体为例,先从一个面看过去,然后以垂直方向为转轴旋转视角±45°,接着以水平方向为转轴旋转视角约±35.264° (准确来说是 arcsin 1⁄√3)。值得注意的是,平面上正方体(右图左上)的边界恰好是一个正六角形:所有黑线的长度相同,而且正方体每一面的面积相同。等角格纸可以在不需要计算的情况下帮忙达到目标。
等角的观点也可以想成是:从一个正方体空间的顶点,看向对面的顶点。x轴向右下延伸、y轴向左下延伸、z轴向上延伸。沿个轴的线彼此成120°。
数学
[编辑]有8种可能的视角符合等角,取决于观察者的卦限。以第一挂限为例,三维上的点ax,y,z等角投影到二维上成点 bx,y,数学上可以写成旋转矩阵:
其中 α = arcsin(1⁄√3) ≈ 35.264° 且 β = 45°。
接着正投影到xy平面:
另外7种符合等角的视角,可以借由旋转反方向或镜像来达成。[1]
历史与限制
[编辑]等角的概念存在了数个世纪,最早由William Farish(1759–1837)在1822年形式化。[2][3] 十九世纪中期,等角投影成为工程师重要的工具。不久之后等角投影和轴测投影被加入欧美国家的建筑学课程中。[4] 然而,轴测投影发源于中国。在它对中国艺术的功能,就如同透视投影之于西洋艺术。轴测投影和相关的绘图法则对电脑图形学 有所帮助。[5]
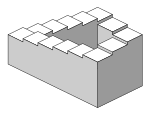
如同各种平行投影的方法,等角投影所绘制的物体不会因为远近而改变大小。虽然建筑制图等时候,需要直接测量长度,但却会造成视觉上失真。不像透视投影呈现眼睛和照相机的结果。等角投影有时会造成高度难以识别(如右左下图)。这被用来创造不可能出现的图形,如潘洛斯阶梯。
在电玩和像素画的用途
[编辑]等角投影提供有限的3D效果,在1980~90年代,因为当时的微电脑能够负荷,而被用在早期的电玩中。
参见
[编辑]注释与参考
[编辑]- ^ Ingrid Carlbom, Joseph Paciorek , Dan Lim. Planar Geometric Projections and Viewing Transformations. ACM Computing Surveys (ACM). December 1978, 10 (4): 465–502. doi:10.1145/356744.356750.
- ^ Barclay G. Jones (1986). Protecting historic architecture and museum collections from natural disasters. University of Michigan. ISBN 0-409-90035-4. p.243.
- ^ Charles Edmund Moorhouse (1974). Visual messages: graphic communication for senior students.
- ^ J. Krikke (1996). "A Chinese perspective for cyberspace?". In: International Institute for Asian Studies Newsletter, 9, Summer 1996.
- ^ Jan Krikke (2000). "Axonometry: a matter of perspective". In: Computer Graphics and Applications, IEEE Jul/Aug 2000. Vol 20 (4), pp. 7–11.